Intro
The following Resecurity report will explore the Qilin ransomware-as-a-service (RaaS) operation’s reliance on bullet-proof-hosting (BPH) infrastructures, with an emphasis on a network of rogue providers based in different parts of the world. Qilin is one of the most prolific and formidable threat groups extorting organizations today. Most notably, they recently claimed responsibility for the September ransomware attack that crippled operations and manufacturing functions at Japanese brewing conglomerate, Asahi Group Holdings, for nearly two weeks.
Qilin’s use of prominent BPH providers, highlights the latter’s role as critical infrastructure for cybercriminal operators. Rogue BPH services enable their clients to host content with minimal or no oversight. Frequently incorporated in pro-secrecy jurisdictions and structured across complex webs of anonymous and geographically distributed shell companies, BPH services are designed to be resilient to abuse complaints and even law enforcement intervention.
Their business model thrives on zero KYC (Know Your Customer) and a total absence of due-diligence checks, effectively creating safe havens for cyber-offenders who wish to remain anonymous. These malign infrastructures, and the pro-corporate secrecy regimes that shield them, enable destructive ransomware campaigns and other malicious cybercriminal operations to persist undisturbed for prolonged durations.
What is Qilin Ransomware?
Qilin is a highly sophisticated Ransomware-as-a-Service (RaaS) operation that first emerged in mid-2022, initially using the name "Agenda." The group rebranded to "Qilin" later that year. According to the Health Sector Cybersecurity Coordination Center (HC3), Qilin ransomware has “variants written in Golang and Rust, and is known to gain initial access through spear phishing, as well as leverage Remote Monitoring and Management (RMM) and other common tools in its attacks.”
Qilin is also “known to practice double extortion, demanding ransom payments from victims to prevent data from being leaked,” according to HC3. The gang’s moniker, Qilin, refers to a mythical creature from Chinese folklore that combines features of a dragon and a horned beast, often compared to a unicorn. However, the operation is believed to have roots in Russian-speaking cybercriminal forums and is structured around a RaaS model, where core developers provide the ransomware infrastructure and tools to a network of affiliates.
These affiliates, who are recruited via underground forums, carry out the actual attacks and share ransom payments with the operators - typically keeping 80-85%, while the operators take 15-20%. The gang has gained widespread notoriety for their malicious ransom campaigns targeting healthcare organizations, government entities, critical infrastructure operators, and asset management firms. Most notably, however, is the gang’s crippling breach of the Japanese brewer Asahi Group Holdings in late September 2025.
Qilin’s RaaS platform allows affiliates to configure attacks, manage victims, and negotiate ransoms via a user-friendly panel. The group maintains a Data Leak Site (DLS) on Tor for publishing stolen data and pressuring victims. Qilin has targeted a wide range of organizations across multiple sectors and geographies, with a focus on high-value targets where disruption is costly, and data is sensitive.
The group is also responsible for a significant number of hack-and-leak incidents and active recruitment of access brokers and affiliates. Microsoft reported actors from North Korea joined the group some time ago, and may include other foreign actors. In fact, one of the most interesting and less widely detailed sides of Qilin is its strong connection to an underground bulletproof hosting conglomerate with origins in Russian-speaking underground and Hong Kong (China). Resecurity is sharing collected intelligence to increase awareness within the cybersecurity community given the gang’s heightened activity.
Cyberattack on Japan
Qilin ransomware group claimed responsibility for the September cyberattack on Japan's Asahi Group Holdings, the country’s largest beverage manufacturer commanding nearly 40% of the national beer market, according to Morningstar. The attack disrupted operations across the conglomerate’s brewing facilities, temporarily halting production and shipping at most of its 30 factories, according to BBC reporting.
Qilin publicly claimed responsibility for the attack and alleged the theft of a substantial amount of data from Asahi's system. As of October 10, all of Asahi Japanese facilities have partially reopened but its computer systems are still down.
Asahi confirmed that the disruption was caused by a ransomware attack and acknowledged evidence of data exfiltration. The incident led to interruptions in order processing, shipping, and customer services.Qilin later published internal documents and claimed to have stolen 27 GB of data from Asahi.
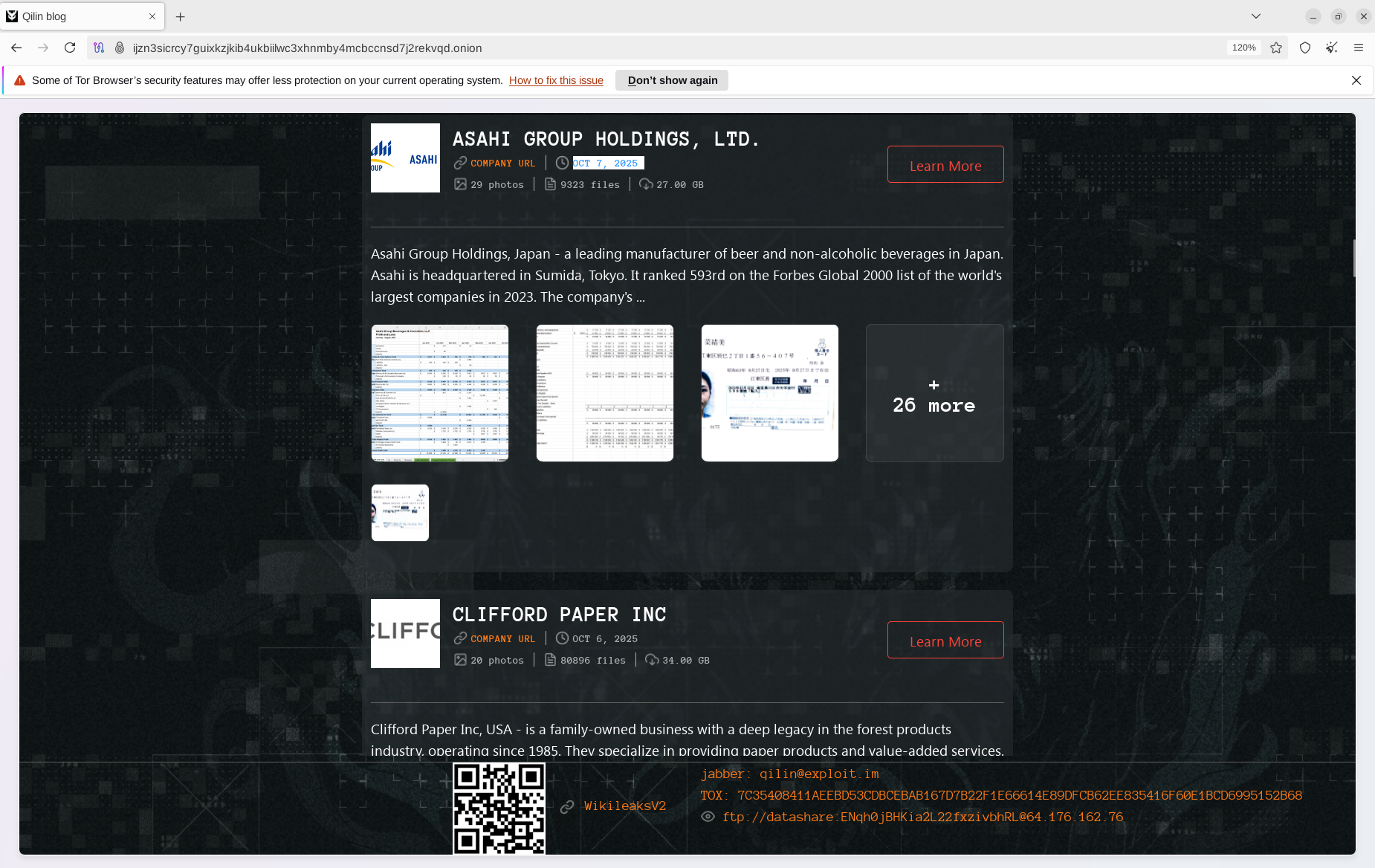
The Qilin ransomware attack, presumably conducted on September 29, 2025, paralyzed Asahi’s digital order placement, shipment, and customer service systems, forcing the company to halt production at most of its 30 factories nationwide. Asahi had to revert to manual processes (phone, fax, hand-written orders) to maintain supply—an inefficient measure that fell far short of meeting demand during the digital outage.
The attack led to nationwide shortages of Asahi products, with major retailers and restaurants reporting out-of-stock items. The company also postponed the launch of 12 new products due to the ongoing system outage. The digital logistics and order management systems were paralyzed, causing significant supply chain bottleneck.
In terms of impact, the incident bears striking similarities to the Trinity of Chaos’ recent ransomware attack on JLR (Jaguar Land Rover), which halted production at all its major plants globally, including facilities in the UK, Slovakia, Brazil, and India. Manufacturing and IT systems were shut down, leading to a complete stoppage of vehicle assembly lines. Both companies suffered substantial financial losses due to halted production, supply chain disruptions, and lost sales. While JLR’s lost sales were estimated to approach £72 million ($97 million) per day, Asahi faced the prospect of an 83% drop in domestic operating profit in the event of a prolonged outage.
Notably, Resecurity HUNTER (HUMINT) investigators engaged in private conversations with Qilin operators and learned the threat actors are attempting to sell the stolen Asahi data for $10 million USD.
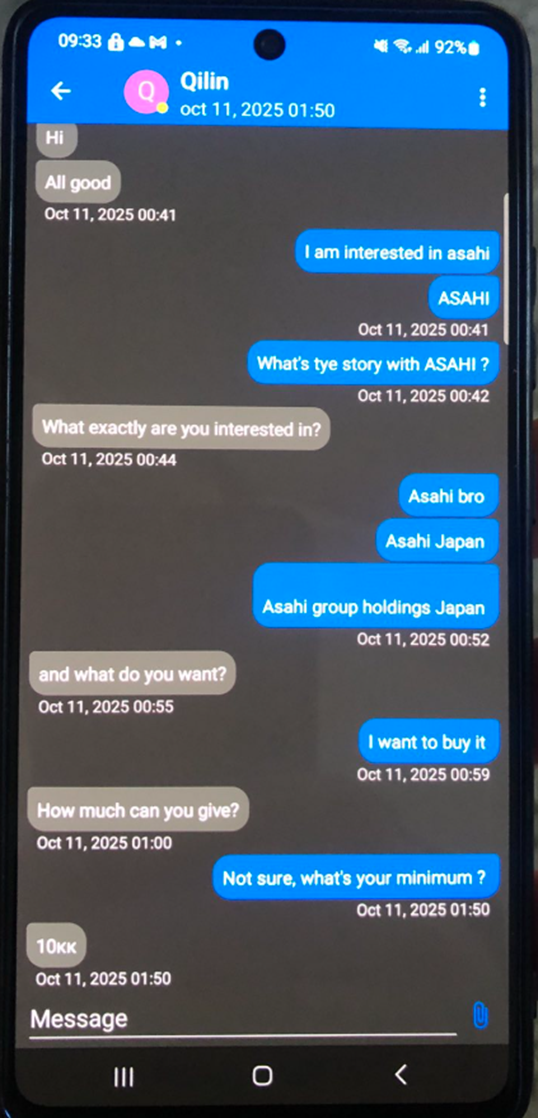
These demands were received on October 11, following the Asahi operations disruption, what is likely one of Qilin's tactics to exclude middlemen and accelerate pressure on the victim.
New Victims Announced
New targets and confirmed victims have been announced by Qilin today (October 15), including but not limited to:
- The Spanish Tax Administration Agency (Agencia Tributaria), the revenue service of the Kingdom of Spain
- Centurion Family Office Services LLC, USA
- Rasi Laboratories, a manufacturer and developer of nutraceuticals, specializing in dietary supplements like capsules, tablets, probiotics, and functional foods, USA
- Victory Christian Center, a community-focused church located in Tulsa, OK, USA
- Richmond Behavioral Health Authority (RBHA), a statewide organization dedicated to providing comprehensive mental health, mental retardation, substance abuse and prevention services to the residents of the City of Richmond
- Turnkey Africa, a leading provider of technology solutions for the insurance industry across Africa
- Charles River Properties, USA, a real estate brokerage based in Waltham, Massachusetts
- New Jersey Property-Liability Insurance Guaranty Association, USA
- Commune De Saint Claude, a municipal services body
- Ville-Elne, a commune in the Pyrénées-Orientales department in southern France.
The Spanish Tax Administration Agency is especially notable among the new victims. This agency employs more than 26,000 staff and operates with a budget of $1.5 billion, processing vast amounts of data from both private and public sectors.

